Introduction
KVM is a full virtualization solution for x86 processors supporting hardware virtualization (Intel VT or AMD-V). It consists of two main components: A set of Kernel modules (kvm.ko, kvm-intel.ko, and kvm-amd.ko) providing the core virtualization infrastructure and processor specific drivers and a userspace program (qemu-kvm) that provides emulation for virtual devices and control mechanisms to manage VM Guests (virtual machines). The term KVM more properly refers to the Kernel level virtualization functionality, but is in practice more commonly used to reference the userspace component.
KVM is an open source software using which you can run multiple virtual machines that are running unmodified Linux or Windows images. Each virtual machine has a private virtualized hardware i.e., a network card, disk, graphics adapter, etc.
VM Guests (virtual machines), virtual storage and networks can be managed with libvirt-based and QEMU tools. libvirt is a library that provides an API to manage VM Guests based on different virtualization solutions, among them KVM and Xen. It offers a graphical user interface as well as a command line program. The QEMU tools are KVM/QEMU specific and are only available for the command line.
When you install the KVM module, it creates a bare metal hypervisor on the Linux kernel. You can then load virtual machine images onto the hypervisor, running separate operating systems. The KVM architecture hosts the virtual machine images as regular Linux processes, so that each virtual machine image can use all of the features of the Linux kernel, including hardware, security, storage, and applications.
The following illustration shows the main components of a KVM Server host.
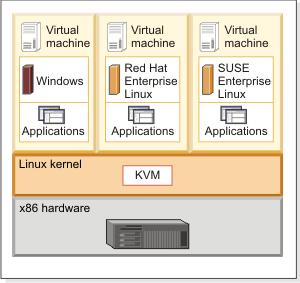
Figure 1 : The architecture of a KVM Server
You can use any type of storage that is supported by Linux to store virtual machine images, including local disks, SCSI, or network-attached storage such as NFS and SAN. The KVM hypervisor also supports virtual machine images on shared file systems such as the Global File System (GFS2) allowing the images to be shared by multiple hosts.
With the KVM hypervisor, you can perform live migrations and move a running virtual machine between physical hosts with no interruption to service. You can save the current state of a virtual machine to disk so that you can restart running the virtual machine from its previous state at a later time.
Because the KVM architecture hosts the virtual machine images as regular Linux processes, you can use the standard Linux security measures to isolate the images and provide resource controls. The Linux kernel includes SELinux along with sVIRT to isolate virtual images. In addition, you can use control groups (cgroups) to further restrict a set of tasks to a set of resources and monitor resource use. For more information about securing your KVM environment, see KVM security.
You can protect and secure the Kernel-based Virtual Machine (KVM) environment by deploying KVM security features, such as configuring network isolation, securing storage devices, configuring secure remote management and isolating virtual machines with the issues.
The KVM architecture supports the memory management features of Linux. In addition, with Kernel Same-page Merging (KSM) virtual images can share memory pages. If the virtual images have identical memory pages, those pages are merged into a single page that is then shared by the virtual images.
The KVM hypervisor supports a variety of guest operating systems, including Linux distributions, Microsoft Windows, and other platforms including OpenBSD, FreeBSD, OpenSolaris, Solaris x86, and MS DOS.
